What better day, May the 4th, to take inspiration from Star Wars as you continuously work hard to be always one step ahead of cyber attackers?
“Ready are you? What know you of ready?”
Yoda to Luke Skywalker [The Empire Strikes Back]
Star Wars Day, May 4, is observed by fans across the world. The date was chosen for the pun on the catchphrase “May the Force Be with You” as “May the Fourth Be with You”.
The reference was first used on May 4, 1979, the day Margaret Thatcher took office as Prime Minister of the United Kingdom. An online news article from the Danish public broadcaster says her political party placed a congratulatory advertisement in The London Evening News, saying “May the Fourth Be with You, Maggie. Congratulations.”
Do organizations today count on the same “Force” wished to the “Iron Lady” to defend from cyber attackers? Are they ready to protect their critical assets – their “crown jewels” – from the scariest known or never-seen-before attacks to the ones caused by mere poor IT hygiene?
Attentive to Your CISO Are You?
If the Death Star were a real-world organization, Admiral Wilhuff Tarkin – who is responsible for supervising the operation of the battle station – would be the General Manager. It is really surprising that he pays absolutely no attention to any warnings regarding security risks, remarked an article by Panda Security.
At the end of Stars Wars: A New Hope, when rebels attack the Death Start, a member of the battle station’s crew – equivalent to a CISO or a member of the IT security team – warns Tarkin of potential vulnerabilities. Had the Admiral been more receptive to these cyber security recommendations, he would have evacuated all personnel from the space station.
To Fight the Dark Side, Purple You Must Go
“When you look at the dark side, careful you must be … for the dark side looks back.” Possibly one of Yoda’s most famous quotes across the Star Wars movies that we can use to describe how wise organizations should see themselves through the eyes of cyber attackers and act. How? Simulation followed by remediation.
The result of cyber attack simulation is that you can check possible routes and types of attack vectors – from the attacker’s perspective – to see where the organization is at risk and take actions to remediate. The best part is that some cyber attack simulation tools allow you to automate the action.
Breach and Attack Simulation (BAS) tools allow organizations to continually and consistently simulate the full attack cycle against their infrastructure, using software agents, virtual machines, and other means.
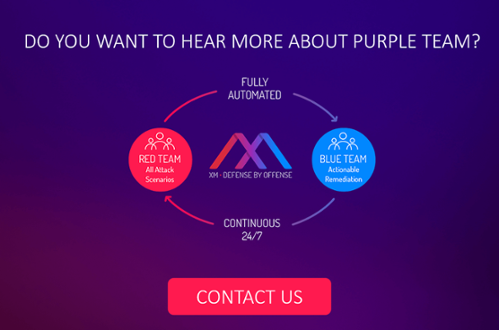
Because many red and blue teams (the company’s own IT personnel who defend their organization’s around the clock) have worked very much in silos and sometimes can get out of sync with each other, the purple team concept was established to enhance red and blue teams’ existing capabilities and allow them to exchange ideas, observations and insights more productively.
With Automation, Purple Team You Crown
Because you don’t happen to have lightsabres or laser blasters to defend yourself and you can’t count on Luke Skywalker, Han Solo or Chewbacca to join your blue team, you need an automated purple team running continuously to follow prioritized remediation guidelines and know as soon as an issue has been resolved.
The move to automation empowers organizations with the ability to gain a worm’s eye view into new back doors and blind spots as soon as they appear and move to remediate them immediately without delay.
XM Cyber’s HaXM is the first fully automated Advanced Persistent Threat (APT) simulation and remediation platform to continuously expose attack vectors, from breach point to any organizational critical asset. This continuous loop of automated red teaming is completed by ongoing and prioritized actionable remediation of security gaps.
In effect, the solution operates as an automated purple team that fluidly combines red team and blue team processes to ensure that organizations are always one step ahead of the hacker. Addressing real user behavior, poor IT hygiene and security exploits, HaXM continuously leverages advanced offensive methods to expose the most critical blind spots.
May the Fourth Be with You Against Cyber Attackers!
Related Topics