End-to-end Exposure Management Across the Hybrid Enterprise
Gain a holistic visibility and analysis of attack paths that span across on-prem and multi-cloud environments to fix the most critical exposures and stop attacks before they happen.
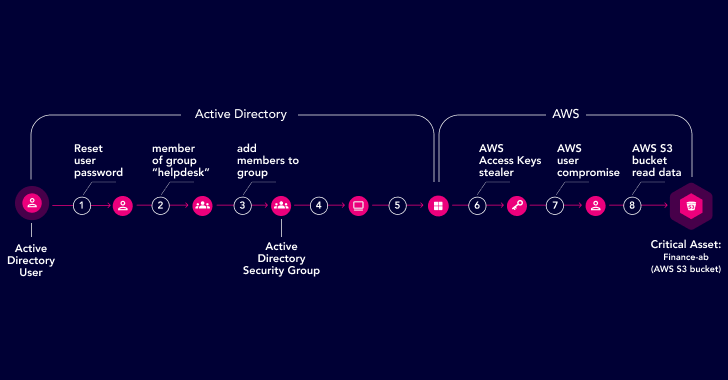
Key Product Features
Supply Chain and Third Party Risk Management
Move beyond compliance and ad-hoc penetration testing to a continuous view of risk when a connected third party you use is compromised, and reduce your attack surface.
Key Product Features
Supply Chain and Third Party Risk Management
Move beyond compliance and ad-hoc penetration testing to a continuous view of risk when a connected third party you use is compromised, and reduce your attack surface.









