I am super passionate about Jiu-Jitsu and InfoSec. I have been involved in InfoSec for 18 years, and Jiu-Jitsu for 10. So how am I drawing the similarities between these two art forms? Both are based on the concept of – offense and defense. In Jiu-Jitsu, you need to have a good offense along with a solid defense. When you start out, you first learn principles and techniques of a good defense. And you hone that skill until you are able to start exerting your offense tactics. As you focus on the basic techniques and methods, you will progress in your Jiu-Jitsu journey and as you become well versed in both defensive and offensive moves, you will be able to practice at a much higher level. It is a true ebb and flow or yin and yang art form.
For example, when you “roll” with someone on the practice mat and work with your partner and “training” on techniques, you talk to each other on what he/she did wrong and/or right and what you did wrong and/or right to point out any weakness and reinforce strengths for your sparring partner. Always use positive reinforcement! That symmetry of a “free roll”, NO EGO and always with an open mind, accelerates your growth on the mat in Jiu-Jitsu. (Do you see any similarities yet?)
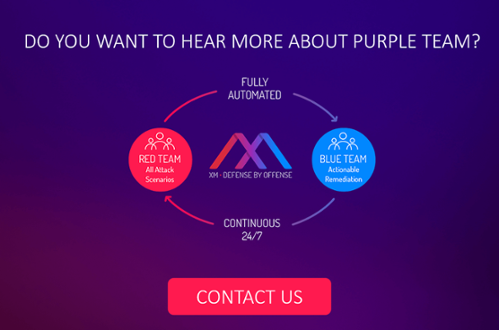
Now, let’s take the Jiu-Jitsu symbiotic relationship of working together and translate that into red and blue teams’ exercises. Both teams can (and do) learn from each other. They learn what each team is doing well, and what each team is not doing to the best of its ability. For some teams, it can take a long time to pull together the right resources and information to pull off an “exercise”. Those exercises are critical to understand what needs to be addressed in a vast enterprise in order to protect its critical assets.
In comes HaXM by XM Cyber! I see this platform as such a creative and unique offering for companies to create a constant feedback loop for red and blue Teams. It’s a way that you can show your teams the campaigns running in a ‘battlefield’ simulation, and detail the attack paths to your crown jewels and how a red team, a pen-tester, or a bad actor can leverage specific security holes to move laterally and compromise your critical assets. HaXM also gives your blue team the ability to see exactly the most critical security issues that need to be fixed, in a priority-based list, in order to stop the potential progress by a red team, a pen-tester or bad actor. This platform better enables companies to build a solid, relatable relationship between the two teams– shoulder to shoulder, with positive reinforcement for both teams and the organization.
Related Topics