Quickly moving to a remote workforce can easily cause gaps in your security. Criminals are seizing the moment and flooding the internet with fake domains and phishing emails to gain access to your employee’s systems and credentials.
XM Cyber can immediately help you identify gaps in security as a result of new work-from-home initiatives. In just minutes after remotely installing our platform, you’ll be able to map your network and see any attack paths that hackers can use to reach your critical assets.
Implementing new VPNs and quickly making changes to your network raises the risk of security issues resulting from misconfigurations, vulnerabilities and human error. Deploy XM Cyber now with no onsite visits required and see results in your live environment in a matter of minutes.
Run security remotely and stop hackers now
- Install and run remotely
- Immediately map your network and all security problems
- Prioritized remediation reports show you what to fix first
- Continuously scan your network like a hacker
- Run safely with no impact to your production network
- Replace onsite penetration testing
- Stop attacks that start from bring-your-own-device requirements
Run Security Tests Remotely and Safely
Take control of your new network environment with XM Cyber’s powerful, remote security platform. Hackers are desperately trying to breach your environment through your employee’s home computers and VPNs. Manual testing is not effective enough because your network is constantly changing. To truly understand your risk, you need to run 24/7 in your production environment, constantly improving your security posture. Plus, now you need to run remotely.
XM Cyber gives you the ability to see your network the way the hacker sees it. It helps you to find all existing hidden vectors of attack, including those that typically go under the radar of most protective measures. And once an attack path is identified, XM Cyber delivers a focused and prioritized remediation report so you can fix those weaknesses before the hacker strikes.
Think Like a Hacker to Stop a Hacker
- Remote – Install and run remotely.
- VPN Safety – Stops hacks originating remotely.
- Immediate – See your security gaps right away.
- Prioritized – Secure your most important data first.
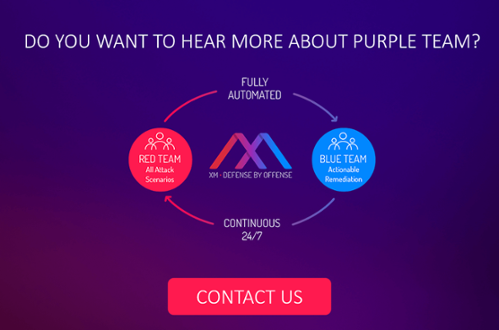
- Red Team – Run red and blue team exercises.
- Lower Risk – Confirm no attack paths can reach critical assets.
Use Cases
- VPN and Home Computers – Assure VPNs don’t open gaps originating from unprotected home machines.
- Remote Pen Test – No onsite visits required to safely test your defenses.
- Remote Red and Blue Teams – Apply the latest attack methods safely and remotely to see where gaps are appearing in your network. Then remediate those gaps with a prioritized blue team report.
- IT Hygiene Testing – Change causes errors. Rely on XM Cyber to identify problems as a result of misconfiguration, vulnerabilities and human error.
- Cloud Security – Protect your cloud assets and assure that breaches cannot move from your on-premise network to your cloud.
DOWNLOAD NOW – English, German, Spanish and Portuguese
Click here to download our brochure with the information above.
Related Topics