What is CTEM?
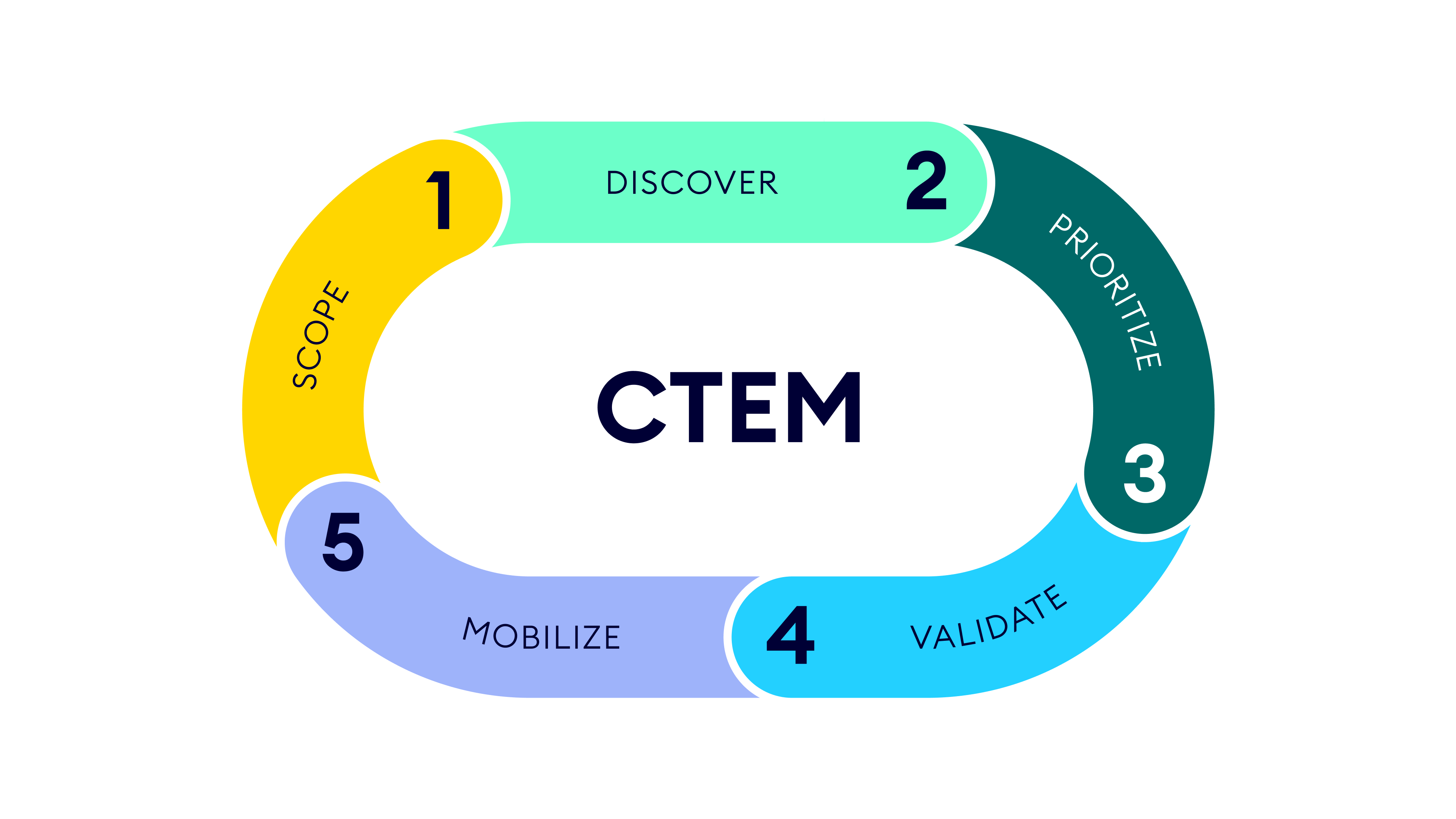
Continuous Threat Exposure Management (CTEM) is a proactive and continuous five-stage program, or framework, that reduces exposure to cyber attacks. It helps organizations identify vulnerabilities and exposures, correlate them to potential attack paths, prioritize them based upon their risk to critical assets, and monitor progress as they implement remediation activities. Organizations worldwide are leveraging CTEM to efficiently address exposures and improve their security posture.
CTEM continually assesses an organization’s entire ecosystem–including networks, systems, assets, and more–to identify exposures and weaknesses with the goal of reducing the likelihood of these weaknesses being exploited. Having a CTEM program can enable continual improvement of security posture by identifying and remediating potentially problematic areas before attackers can exploit them.
The “continuous” element of CTEM refers to a give-and-take relationship between the CTEM program and the associated risk remediation efforts, wherein data stemming from both aspects informs processes to make ever-more optimal decisions about how to manage exposure risk. According to Gartner® in their report Implement a Continuous Threat Exposure Management (CTEM) Program, Published 21 July 2022, “The objective of CTEM is to get a consistent, actionable security posture remediation and improvement plan that business executives can understand and architecture teams can act upon.” The fundamental objective of CTEM is to lower the probability that weaknesses will be leveraged.
What are the 5 stages of CTEM?
CTEM is an umbrella program that implements an approach to exposure reduction. Accordingly, it isn’t a product or service, but the right product(s) can help implement it in your organization. The five stages of CTEM are described below.
Stage 1 Scoping
This first stage encompasses understanding your attack surfaces and how important each asset is to your business, both of which will change over time. It includes identifying key attack surfaces, and it requires input from various decision-makers, such as leaders from IT, Legal, GRC, Dev, R&D, Product, and Business Ops teams.
Stage 2 – Discovery
The discovery stage consists of assessing each asset for potential exposures and analyzing how the exposures correlate particular risks. This extends beyond just standalone vulnerabilities in that it includes other types of exposures – such as Active Directory, identity and configuration risks – as well as how exposures can be chained together to enable attack paths towards assets.
Stage 3 – Prioritization
In the prioritization stage, the exposures are analyzed to weigh the level of known threat they’ve posed ‘in the wild’ and the importance of the assets directly impacted.
This step is crucial, because large organizations uniformly find that there are far more exposures than they’ll ever be able to fix. Why? Partly because of sheer volume, and partly because their environments are constantly changing – new assets, users, software, configuration settings, and more.
Prioritization has traditionally been limited to vulnerabilities, excluding other exposure types, such as identities and misconfigurations. And it hasn’t considered how the exposures relate to potential attack paths to critical assets. With CTEM, prioritization makes clear which remediations are most beneficial for reducing the greatest amount of risk to critical assets.
Stage 4 – Validation
The validation stage looks at how attacks can occur and the likelihood of their occurrence. This step can leverage a variety of tools for different uses. In some cases, validation is performed to enable prioritization, as in Stage 3 above. In other cases, validation can be valuable in continually testing security controls or to automate periodic pen testing.
Stage 5 – Mobilization
This stage, which in a sense serves as the facilitating factor for the entire framework, is where you make sure everyone is on the same page and understands their role and responsibilities within the context of the program. Mobilization is optimized when both the security team and the IT teams involved in remediation have clarity around the risk reduction value of any remediation effort, as well as reporting to show the overall trend of improvements made to security posture over time.
What problem is CTEM solving, and why now?
Organizations implement CTEM because otherwise, they are faced with the following frustrating situation:
- When they execute a comprehensive discovery, they find an overwhelming volume of exposures – far more than they can actually fix, and some of which they simply can’t fix.
- The exposures are typically separated into different lists based on the tools available for different types of exposure, and for different environments – on-premise, cloud, container, traditional vulnerability, configuration issue, identity exposure, Active Directory issue, and more.
- Organizations have no way to aggregate the exposures, place them into context according to actual risk (based on how an attacker can exploit the current configuration of their environment), and prioritize remediation activities. So, they waste time on fixing exposures that don’t matter, or they essentially give up.
- Furthermore, where they do make progress, they have no way to correlate it to overall organizational risk, or to illustrate how their efforts are making a difference.
All this is despite decades of using traditional vulnerability management tools, and even more recent breach and attack simulation (BAS) tools. The failure of these tools to protect against attacks is a primary reason that CTEM is a top priority now.
| Feature | Traditional RBVM | XM Cyber Continuous Exposure Management |
| Focus | Prioritizes vulnerabilities (CVEs) based on risk | Analyzes all security exposures and attack paths |
| Exposure Types | Primarily CVEs | CVEs, misconfigurations, identity and credential issues. |
| Attacker Perspective | Minimal | Considers attacker perspective and potential exploitation routes |
| Prioritization | Based on individual vulnerability severity and asset criticality | Based on the role of the vulnerability within attack paths, the compromise rate, and the potential business impact risk |
| Efficiency | May patch vulnerabilities attackers wouldn’t exploit | Focuses remediation efforts on vulnerabilities presenting the greatest risk to critical assets |
| Actionable Insights | Minimal guidance on remediation | Provides easy to follow step-by-step remediation playbooks and best practice security guides |
| Overall Approach | Reactive – focuses on patching identified vulnerabilities | Proactive – identifies vulnerabilities and validates their exploitability along attack paths to you critical assets |
| Risk Reduction | Reduces intrusion-risk by addressing high-severity vulnerabilities | Combines intrusion-risk with business impact risk, to drive a significant reduction in overall risk posture. |
Is CTEM is the right solution?
According to Gartner, “CTEM programs expand traditional cybersecurity assessment.” Further, the report also notes that CTEM programs use cybersecurity technology to “Align the scopes of exposure assessment cycles with specific business projects and critical threat vectors.” and “Validate the enterprise’s exposure and remediation priorities by including the attacker’s perspective, and testing the effectiveness of security controls and incident response processes.“ This ensures that security efforts are precisely tailored to the areas that matter most to an organization, enhancing the efficiency and efficacy of security measures. And CTEM provides a holistic view of risk – one that can be tracked over time to correlate remediation activity with posture improvement.
How valuable is CTEM?
The value of CTEM correlates to the size of the problem and the improvements that organizations see when they implement it. In XM Cyber’s own research Navigating the Paths of Risk: The State of Exposure Management in 2023, we find that:
- Larger enterprises can have over 250,000 open vulnerabilities.
- However, research shows that firms only fix about 10% of those open vulnerabilities, leaving the rest in place.
- Yet 75% of exposures don’t lead to another asset – they are “dead ends” to attackers. Furthermore, only 2% lead to critical assets.
Forrester’s Total Economic Impact Study, 2022 finds a 90% reduction in likelihood of a severe breach for those organizations with a proper solution in place, and an ROI of up to 400%.
How popular is CTEM?
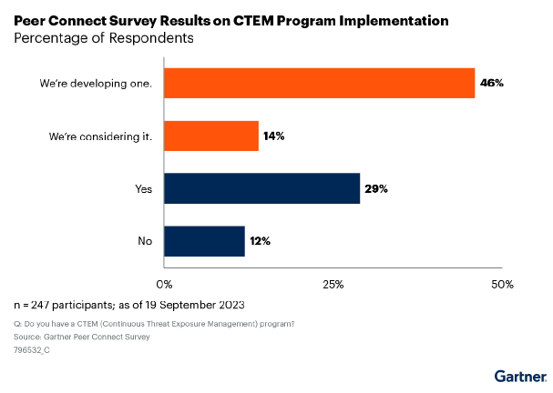
A Gartner report also notes that, “A survey conducted by Gartner Peer Connect1 found that 71% of organizations could benefit from a CTEM approach, with 60% of respondents already pursuing a CTEM program or considering doing so.”
What does Gartner say about CTEM?
“By 2026, organizations prioritizing their security investments, based on a continuous threat exposure management program, will realize a two-third reduction in breaches”, Gartner Top Strategic Technology Trends for 2024: Continuous Threat Exposure Management, Published 16 October 2023
Debunking a common “detection-based” approach, CTEM proposes that focusing on events rather than posture is a losing approach in the long term. Attackers have proven that. Only a prioritized, continuous, threat-based approach will be successful in the long run. In other words: implement CTEM.
Furthermore, as mentioned above, Gartner outlines a five-step process that organizations can follow to properly manage their exposures. As we see it, critical to those steps are the following:
- Going beyond vulnerability management to understand critical assets and how they can be attacked
- Developing an ongoing, continuous process
- Prioritizing findings based on actual risk and impact to the environment, from an attacker’s perspective
- Executing and validating based on the above
How is CTEM different from vulnerability management/RBVM?
Risk-based Vulnerability Management (RBVM) is a cybersecurity strategy designed to help organizations limit risk through the strategic prioritization of vulnerability remediation. To accomplish this, organizations use tools to assess existing cybersecurity vulnerabilities and determine the amount of risk each vulnerability poses to business-critical assets based on known exploitation of vulnerabilities “in the wild”.
Automating this process is certainly essential, given the scale involved, which is why they’ve existed for decades. In 2020, 17,000 new vulnerabilities were reported – a rate that equals one new vulnerability every six minutes. Attackers waste no time seeking to develop exploits, which means that defenders must be equally nimble and fast to respond.
However, defenders using these tools are overwhelmed with the job of managing cyber vulnerabilities. Even large, well-funded organizations can’t patch all the vulnerabilities they discover. There are simply too many vulnerabilities, and there are systems that can’t be patched, as well as supply chain dependencies.
Critically, RBVM is limited to prioritizing only vulnerabilities (CVEs), and doesn’t address identity issues and misconfigurations that attackers regularly exploit.
CTEM dramatically focuses and reduces remediation efforts by prioritizing efforts across all exposure types, not just CVEs, based upon the impact of real risk to critical assets. And it provides a holistic process for managing that risk over time. In this way, CTEM elevates RBVM, augmenting it with broader exposure coverage, real-world attacker information and remediation insights.
How is CTEM different from Red Team exercises?
Red Team exercises are performed to achieve specific goals, such as evaluating the ability of attackers to reach business-critical applications. According to IBM, Red Teaming is “heavily focused on emulating an advanced threat actor using stealth, subverting established defensive controls and identifying gaps in the organization’s defensive strategy. The value of this type of engagement can be derived from a better understanding of how an organization detects and responds to real-world attacks.”
Red Team exercises are valuable to (a) identify and uncover one or more particular attack paths to critical assets and (b) test the ability of defenders to detect the attackers. However, they’re manual exercises that are expensive and only performed periodically. Also, they don’t uncover all the attack paths that could be taken, or prioritize the fixes required to prevent them. In other words, they are good for testing existing defenses, but poor for making regular, comprehensive posture recommendations.
Unlike one-off Red Team exercises, CTEM provides an ongoing, holistic analysis of defenses; it prioritizes remediation efforts to shore them up; and it tracks improvement over time.
How is CTEM different from Penetration Testing?
Penetration testing is similar to Red Team exercises in that both use a testing methodology in an attempt to assess an organization’s cyber defenses. However, pen testing is typically performed periodically during well understood timeframes, and typically looking for known vulnerabilities. Pen tests assess if applications, networks, platforms, and systems can be breached, and are used to find issues that need to be addressed.
As with Red Team exercises, pen testing suffers from an inability to assess the full environment, and it only provides a point-in-time assessment – one that’s lacking in prioritization, and almost immediately out of date. Penetration testing results will deliver highly confident results for a limited scope, but with a highly manual effort.
CTEM provides an ongoing, holistic analysis of defenses; it prioritizes remediation efforts to shore them up; and it tracks improvement over time. In fact, according to the Forrester Total Economic Impact Study, 2022, organizations that use a CTEM-oriented attack path solution can reduce their penetration testing costs of up to $1.4 million over three.
How is CTEM different from Breach and Attack Simulation (BAS)?
Breach and Attack Simulation (BAS) solutions offer a different approach for performing automated security testing. Some BAS tools challenge the existing security infrastructure, while others are designed to test existing security controls to ensure they are working as expected.
Breach and Attack Simulation, pen testing, and Red Teaming all simulate attacks to hypothesize the outcomes of real-world scenarios. They are used to assess and find issues that need to be addressed. Their use, though, is limited by the operational risk they create, as running these live tests can put the security team at risk of creating performance issues- or worse, outages- on production systems. These tools are used periodically across a fraction of the overall environment, leveraging only a subset of all possible attack techniques. While still valuable for finding issues, this approach is incomplete.
A CTEM solution analyzes the complete environment, and it covers a broader array of exposures. It provides an ongoing, holistic analysis of defenses; it prioritizes remediation efforts to shore them up; and it tracks improvement over time.
How is CTEM different from IAM and ITDR solutions?
Identity and Access Management (IAM) and Identity threat detection and response (ITDR) solutions are laser focused on identities. These are critical to an organization’s security posture, since most attacks take advantage of an identity vulnerability somewhere along the attack path. However, they don’t include an evaluation of non-identity exposures, or any ability to determine potential attack paths to critical assets. Thus, their view into an organization’s environment is quite limited.
A CTEM solution analyzes the complete environment, and it covers a broader array of exposures. It provides an ongoing, holistic analysis of defenses; it prioritizes remediation efforts to shore them up; and it tracks improvement over time.
How is CTEM different from External Attack Surface Management (EASM)?
External Attack Surface Management (EASM) is the process of continuously discovering and inventorying the risks of external assets to potential breaches. It’s fully focused on the initial breach points of an attack – your IT environment’s “external surface”. As such, it’s conducted from outside your environment, and it provides no insight into further steps an attacker would take beyond that initial breach.
CTEM looks beyond the surface to understand the full set of exposures in your environment, as well as how an attacker can chain together a set of exposures into an attack path reaching critical assets. CTEM provides a much more complete list of exposures than ASM can provide, and it can give you a much more meaningful assessment of your cyber security risk. Furthermore, CTEM has the context to prioritize those exposures for you so you can remediate with confidence and efficiency.
How is CTEM different from Cloud Security Posture Management (CSPM)?
Cloud security posture management (CSPM) solutions identify misconfiguration issues and compliance risks in the cloud. CSPM helps monitor cloud infrastructure for exposures and gaps in security policy enforcement. Given the growth in the combined IaaS, PaaS and SaaS markets (projected at over 17% annually through 2027), this is clearly an area of importance. In fact, experts project that 99% of records compromised in cloud environments will be the result of user misconfigurations and account compromise.
However, most organizations, especially large ones, have environments consisting of remote employees, on-premises assets, and multiple cloud vendors. So a CSPM is fundamentally a piecemeal solution. It doesn’t provide a holistic view into their security posture, and it can’t prioritize remediation efforts organization-wide. This is particularly important since many attacks involve a compromising a combination of remote assets, on-premise assets, and cloud assets.
A CTEM solution takes all this into account, by incorporating cloud assets into a holistic view of an organization’s environment. Attack path analysis and posture assessment includes all types of assets, and remediation recommendations are prioritized accordingly. Total organizational security is the domain of CTEM.
How do I choose a CTEM vendor?
While CTEM is a strategy rather than a product category, there are several key aspects of solutions that you should evaluate when choosing tools related to CTEM.
Breadth of exposure detection – What different types of exposures does the solution encompass, such as traditional vulnerabilities, misconfigurations, identity issues, and more?
Environmentally comprehensive – Does the solution cover all workstations, entities, virtual machines, containers, user activity, cloud resources, and configurations, etc., as part of analysis to ensure you can see all ways your organization is at risk to plan prioritized remediation efforts?
Risk contextualization – How well does the solution combine its knowledge of exposures, network paths, and critical assets into a view of potential attack paths? And how does it display this information for defenders so that both security and IT teams understand the value of their remediation efforts?
Remediation prioritization – Does the solution analyze potential attack paths and prioritize them by the impact they pose to critical assets, so you know what to fix to disrupt the most damaging attack paths first? And can it detect “dead ends” that don’t need to be fixed in the short term?
Remediation assistance – With its knowledge of exposures and attack paths, can the solution provide concrete remediation guidance to implement fixes, improving both consistency and efficiency?
Continuous evaluation – Given that IT environments are constantly changing, does the solution perform continuous evaluations to detect new exposures and new attack paths that will surely appear? Does it also keep up to date with the latest vulnerabilities and attack techniques? And can it track changes in security posture over time?
Executive reporting – Can the solution combine organization-wide risk assessments and trending information into executive-level reporting, to answer such questions as, “Where are we most vulnerable?” and, “How is our risk posture improving over time?”
Operational safety and impact – How easy is the solution to deploy and manage? And what potential risks, if any, does the deployment have on your production environments?
Another way to evaluate vendors is to consider these questions, and how different vendors answer them.
- Which of my critical assets are at risk today?
- What paths would allow an attacker to reach them?
- Where are all the exposures in my environment?
- Which ones are most important to remediate to protect my critical assets (i.e. choke points)? Which are least important (i.e. dead ends)?
- How can you show me an overall score or assessment of my posture in protecting my critical assets? Can you help me demonstrate improvement over time?
Why should I choose XM Cyber for CTEM?
XM Cyber offers the most comprehensive solution for delivering the value of exposure management – the core capability required for a CTEM program.
XM Cyber uniquely discovers exposures that go beyond traditional vulnerabilities, encompassing a wide range of configuration and identity issues that real-world attackers rely on to succeed.
XM Cyber has the most comprehensive, intelligent approach to analyzing exposures, connectivity, and the value of various assets – across remote devices, on-premise, and cloud. Unlike other approaches to validate exposures, such as Pen Testing, XM Cyber’s approach to validating exposures is safe to run comprehensively across large environments without risk of creating operational issues or false positive alerts. It is the premier solution for attack path detection, prioritization, and communication.
XM Cyber goes beyond one-time detection, continuously providing valuable prioritization and guided remediation, as well executive-level reporting and security posture trending.
All the above help you avoid busy work, implement improvements that protect your assets from real-world attackers, and clearly communicate status and trending to busy executives.
Does CTEM cover both on-premises and cloud environments?
Absolutely. Fundamental to CTEM is a full analysis of exposures and how they impact the risk to critical assets. In almost all organizations, exposures span remote workers, on-premise equipment, and cloud resources. While seemingly separate, these environments are, in fact, highly integrated. And often the assets come from multiple different vendors, with different management systems. To understand attack surfaces, attack paths to critical assets, and overall risk, all these environments must be considered in a holistic way – the way an attacker will view them.
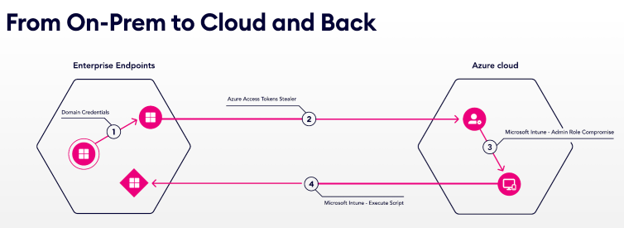
71% of orgs have exposures in their on-prem networks that put their critical assets in the cloud at risk. Once there, 92% of critical assets become vulnerable.
Accordingly, XM Cyber’s CTEM solution encompasses your whole environment.
For more information on how XM Cyber incorporates your cloud environment into a CTEM solution, check out The Power of Attack Paths in the Cloud.
How do I get started with CTEM?
The process of Establishing a Modern Exposure Management Program consists of the following major activities, which can overlap in some cases:
- Initial onboarding and deployment of the software components.
- Critical asset definition, remediation process definition, and mapping to remediation teams.
- Integration of the XM Platform into ticketing systems.
- Identification of attack paths with resulting remediation plan
- Remediation and verification activities
- Executive reporting and security posture improvement
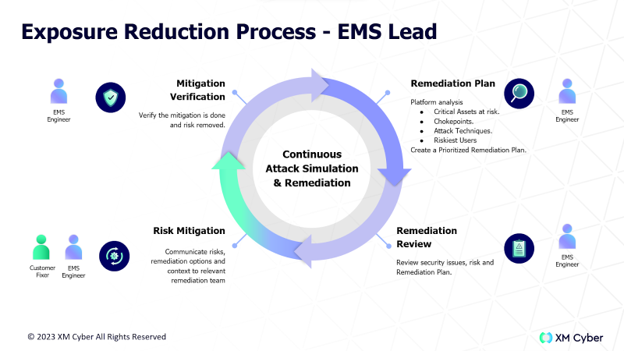
To help this proceed as quickly and smoothly as possible, XM Cyber provides an Exposure Management Service (EMS). EMS extends your existing security team with a designated remediation expert having expertise in continuous exposure management. They proactively drive risk mitigations, and they help improve your operational exposure management and remediation processes. A standard timeline for an EMS engagement in a medium to large enterprise is only a few weeks from initial kickoff to “process wet run”- the point at which remediation is underway.
XM Cyber EMS also provides a variety of deliverables covering education, documentation, remediation guidance, reporting, and periodic reviews. For more information, see XM Cyber Exposure Management Service or email the EMS team directly
Who is benefiting from CTEM now?
Any organization with a formal cyber security program can benefit from CTEM, and adoption is becoming mainstream. Accordingly, a recent Gartner study of 247 organizations found that 29% had already implemented a CTEM program, with another 46% having their CTEM program under development- a 75% “penetration rate” of CTEM into these organizations.
XM Cyber similarly sees many different types of organizations using our solution in support of their CTEM program, including the following examples:
- A leading US insurance firm taking the next step beyond vulnerability scanners and antivirus software.
- A major international port authority looking to gain insight and control into security posture that could be impacted by over 100 local administrators.
- One of the largest retailers in the world, with over 500,000 employees, improving the efficiency of remediation, and better coordinating activities between security and IT teams.
FAQ
How did XM Cyber identify and map the specific attack techniques within the Okta environment that are discussed in this series?
XM Cyber identified and mapped the specific attack techniques within the Okta environment discussed in the series by conducting in-depth security assessments and analysis of Okta environments. This involved exploring and exploiting various vulnerabilities and misconfigurations in Okta’s Role-Based Access Control (RBAC) and other components. They likely utilized a combination of manual testing, automated tools, and their expertise in cybersecurity to discover how attackers could leverage weaknesses to escalate privileges, gain unauthorized access, and move laterally within a network. Their research and findings are often shared through detailed blog posts or reports, aiming to raise awareness and help organizations strengthen their security posture.
Are there any real-world examples or case studies where these misconfigurations in Okta’s RBAC (Role-Based Access Control) module led to significant security breaches or incidents?
Regarding real-world examples or case studies, while the specific details of incidents related to misconfigurations in Okta’s RBAC leading to security breaches are not always publicly disclosed, there have been several high-profile breaches where identity and access management systems played a role. For instance, in various instances, attackers have exploited misconfigurations and weaknesses in identity management systems to perform credential stuffing attacks, gain unauthorized access to sensitive systems, or escalate their privileges within a network. These incidents underline the importance of properly configuring and managing access controls to protect against unauthorized access and potential data breaches.
Aside from misconfigurations by IT staff, are there other common vulnerabilities or weaknesses within the Okta environment that attackers commonly exploit, and will those be covered in future blog posts?
Aside from misconfigurations by IT staff, other common vulnerabilities or weaknesses within the Okta environment that attackers commonly exploit include vulnerabilities in third-party applications integrated with Okta, phishing attacks targeting Okta users to steal credentials, and exploiting outdated or weak protocols. Attackers may also target API keys or tokens that are not securely managed, as well as taking advantage of any lack of multifactor authentication on critical accounts. XM Cyber and other security researchers are likely to cover these and other vulnerabilities in future blog posts, as part of their ongoing efforts to educate and inform about cybersecurity risks and how to mitigate them. Continuously identifying and addressing new vulnerabilities is crucial for maintaining the security of Okta environments and protecting sensitive information.